FAQ
SIP
Session Initiation Protocol – SIP
What is SIP
SIP is an acronym for Session Initiation Protocol. That is, it’s a signaling protocol for initiating (and terminating) multimedia sessions such as voice calls and video conferences.
What’s so great about SIP and why is everyone talking about it? Well, for one thing, SIP opens the door to multi-user multimedia sessions from any SIP-enabled device to any other. Multi-user means that cell phones, smartphones, IP phones and computers can all join a single session at the same time. Multimedia means it no longer has to be a voice or video or instant messaging, it can be a voice AND video AND instant messaging.
Secondly, SIP saves money. Because it’s based on IP (Internet Protocol) and travels over standard IP transit protocols, SIP can share the same network connections as data communications instead of requiring costly, dedicated voice circuits. How much money can you save with SIP? For large enterprises, the annual savings can be in the millions of dollars. Maybe they should have called it GULP instead!
The Story of SIP: A Very Brief History
In order to take advantage of what many people saw as a global shift toward IP communications and applications, SIP is based on existing Internet protocols like HTTP, TCP, SMTP and technologies like Domain Name Servers. And they were right;
Today, there is a marked migration away from dedicated voice networks like the traditional telephony system and toward converged voice/data/video networks over IP. By basing SIP on existing IP standards, it’s now easier than ever to build voice enabled multimedia applications.
SIP: The Super Signaling Protocol
A multimedia session such as a Voice over IP (VoIP) call or video conference consists of two main parts: the signaling and the media. Think of when you meet someone for the first time: you might begin by making eye contact, shaking hands, exchanging names, followed by a conversation and, finally, say goodbye to one another. Multimedia sessions work much the same way: the conversation itself is the media part and everything else (from hello to goodbye) is the signaling part.
SIP accomplishes several things during a session:
>> It locates the other device(s) you want to talk with on any network;
>> It initiates and terminates the session;
>> It handles changes to the session like adding new users or new kinds of media (e.g., adding video to a voice call);
>> It negotiates session capabilities between devices (e.g., which voice or video codecs will be used).
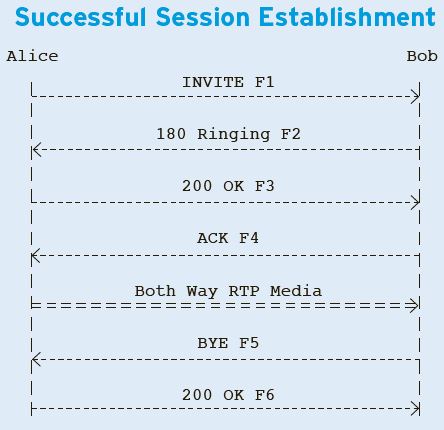
A Sample SIP Call Flow
A basic SIP call flow between two SIP devices is fairly straightforward and involves only a handful of messages that mimic the way a traditional call is made. These messages include the invitation (called a SIP INVITE), the generation of a ringing sound on the caller’s device, an acknowledgment (ACK) when the called SIP device answers, and the session termination (BYE). In between is the two-way passage of RTP media. A sample call flow between Alice and Bob, for example, would look like this:
SIP Sessions in an IP Network
In addition to a SIP-enabled phone or computer (known as a SIP User Agent), SIP sessions rely on several network elements to help them initiate and terminate calls. These include a SIP Registrar Server to locate the IP address of the SIP User Agent being called, a SIP Proxy Server to send the SIP message to the IP address and, in the case of sessions that involve more than one network, a SIP Redirect Server to help forward the SIP message to a peer network’s SIP Proxy Server.
1. When a phone number is dialed, the SIP User Agent sends a SIP message to the Proxy Server in Network A.
2. The SIP Proxy Server queries the SIP Redirect Server in Network A for the location of the Proxy Server in Network B.
3. The SIP message is then forwarded from the Proxy Server in Network A to the Proxy Server in Network B.
VoIP
Voice Over Internet Protocol – VoIP
What is VoIP
Introduction: VoIP is an acronym for Voice Over Internet Protocol, or in more common terms phone service over the Internet.
If you have a reasonable quality Internet connection you can get phone service delivered through your Internet connection instead of from your local phone company. Some people use VoIP in addition to their traditional phone service, since VoIP service providers usually offer lower rates than traditional phone companies.
How does VoIP work? What happens when you make a VoIP call?
When a VoIP call is made, your voice goes through the following process:
1. Your voice (analog) is sent from your regular telephone to a device called an Analog Telephone Adapter (ATA). The ATA converts your analog voice into digital samples through the use of an Analog-to-Digital Converter (ADC). The ATAs are usually provided by your VoIP service provider when you sign up for service.
Note: If you have one of the new digital IP telephones that are now available on the market, there is no need for the ATA device since the ADC function is performed inside the IP telephone.
2. The digital bits must now be compressed into a standard format which can be transmitted faster and more efficiently. In VoIP, digital signal processors (DSPs) perform this compression using codecs which segment the voice signal into frames and store them in voice packets.
Some compression standards and associated bandwidths are listed as follows:
o PCM, Pulse Code Modulation, Standard ITU-T G.711, 64Kbps
o CS-ACELP, Standard ITU-T G.729 and G.729a, 8Kbps
o ADPCM, Adaptive differential PCM, Standard ITU-T G.726, up to 40Kbps
o LD-CELP, Standard ITU-T G.728, 16Kbps
o MP-MLQ, Standard ITU-T G.723.1, 6.3Kbps, Truespeech
o ACELP, Standard ITU-T G.723.1, 5.3Kbps, Truespeech
o LPC-10, able to reach 2.5 Kbps
While standard phones utilize the G711 codec, the G723 codec is emerging as the popular codec choice for IP Telephony applications. This codec is preferred due to its smaller size and higher compression which allows for easier transport over the internet.
3. The compressed data must then be encapsulated within IP packets. VoIP is a Layer 3 network protocol that uses various Layer 2 point-to-point protocols such as PPP for its transport. VoIP protocols typically use Real-time Transport Protocol (RTP) for the media stream or speech path. RTP uses User Datagram Protocol (UDP) as its transport protocol. For IP networks, the reliable service of TCP is not appropriate for real-time applications because TCP uses retransmission to ensure reliability. The IP layer provides routing and network-level addressing; the data-link layer protocols control and direct the transmission of the information over the physical medium.
4. The packets are then transmitted across the internet in compliance with a voice communications protocol or standard such as H.323, Media Gateway Control Protocol (MGCP), or Session Initiation Protocol (SIP).
5. When your IP packet (which contains your speech) arrives at the destination (the telephone that you called) it must go through a similar process mentioned in 1-4, but in reverse. As such the IP packets are de-capsulated or disassembled to retrieve the compressed voice data, which can then be decompressed using the same codec that performed the compression. After the decompression, the original digital data is left which can then go through a digital to analog converter and be returned to its original analog voice format and be clearly heard and understood by your called party.
This entire process is completed in real time such that telephone users do not detect a delay in the speech. The diagram below shows a high level view of how a basic VoIP call is made and the path that the packets travel to reach their destination.
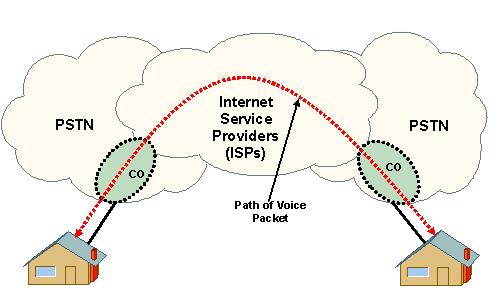
The CO or Central Office connects the local loop from the demarcation point at the VoIP subscriber’s residence. The CO then makes the decision where to send the call. An expanded view of the CO and the PSTN (of which the CO is a part of) is shown in the diagram below. This diagram shows how a typical DSL line is integrated into the network. The topology will be slightly different for other types of broadband connection but the general path of the data packets will be the same when it reaches the CO.
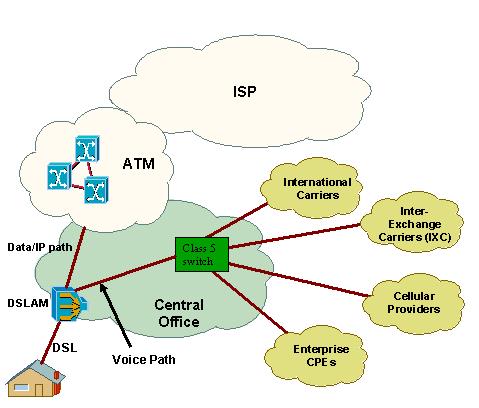
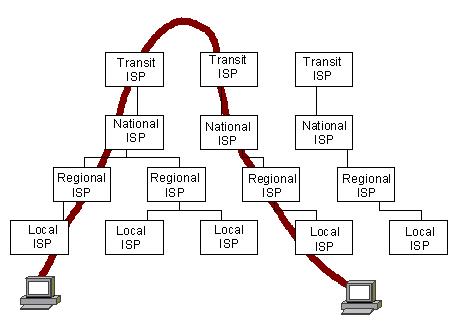
This diagram has expanded the view of the CO and shown some potential destinations for circuit switched voice that goes through the PSTN. This is obviously not where the VoIP packets are destined and as such it is necessary to show an expanded view of the Internet Service Provider (ISP) network since this is where the VoIP packets will be sent to. The diagram below indicates the path of a typical call through the ISP chain.
Hopefully this advanced guide has given you a deeper insight into the inner workings of VoIP. Below you will find related articles for further reading, including an in-depth article on the actual digitization process.
Why use VoIP?
There are two major reasons to use VoIP
• Lower Cost
• Increased functionality
Lower Cost: In general phone service via VoIP costs less than equivalent service from traditional sources. This is largely a function of traditional phone services either being monopolies or government entities. There are also some cost savings due to using a single network to carry voice and data. This is especially true when users have existing under-utilized network capacity that they can use for VoIP without any additional costs.
In the most extreme case, users see VoIP phone calls (even international) as FREE. While there is a cost for their Internet service, using VoIP over this service may not involve any extra charges, so the users view the calls as free. There are a number of services that have sprung up to facilitate this type of “free” VoIP call. Examples are: Free World Dialup and Skype for a more complete list see: VoIP Service Providers
Increased Functionality: VoIP makes easy some things that are difficult to impossible with traditional phone networks.
• Incoming phone calls are automatically routed to your VoIP phone where ever you plug it into the network. Take your VoIP phone with you on a trip, and anywhere you connect it to the Internet, you can receive your incoming calls.
• Call center agents using VoIP phones can easily work from anywhere with a good Internet connection.
ATA
Analog Telephone Adapter – ATA
What is analog telephone adapter (ATA)?
An analog telephone adaptor (ATA) is a device used to connect a standard telephone to a computer or network so that the user can make calls over the Internet. Internet-based long distance calls can be substantially cheaper than calls transmitted over the traditional telephone system, and ATAs are typically cheaper than specialized VoIP phones that connect directly to a computer’s Universal Serial Bus (USB) port.
Whether or not VoIP is cheaper than traditional phone service depends on a number of factors, including the rates charged by the respective service providers and equipment costs. Skype, one VoIP provider, offers free calling locally and between members, and inexpensive long-distance calls to other numbers.
There are several types of analog telephone adapters. All ATAs create a physical connection between a phone and a computer or a network device; some perform analog-to-digital conversion and connect directly to a VoIP server, while others use software for either or both of these tasks.
The simplest type of ATA has one or more RJ-11 jacks to plug a telephone (and/or a fax) into and a USB connector that plugs into the user’s computer, laptop, or handheld device. This type of ATA often works in conjunction with some type of software (typically a softphone program). The software acts as an intermediary between the telephone and a VoIP server, digitizing voice data so that it can be transmitted over the Internet.
In an enterprise setting, an ATA usually has multiple telephone jacks and an RJ-45 connection to a 10/100BaseT Ethernet hub or switch, and is used to connect to a local area network (LAN). Such an ATA digitizes voice data, and uses protocols such as such as H.323 or SIP to communicate directly with a VoIP server so that a softphone is not required. An ATA that connects telephones to a LAN is sometimes called a VoIP gateway.
What is Gateway?
A gateway is a network point that acts as an entrance to another network. On the Internet, a node or stopping point can be either a gateway node or a host (end-point) node. Both the computers of Internet users and the computers that serve pages to users are host nodes. The computers that control traffic within your company’s network or at your local Internet service provider (ISP) are gateway nodes.
In the network for an enterprise, a computer server acting as a gateway node is often also acting as a proxy server and a firewall server. A gateway is often associated with both a router, which knows where to direct a given packet of data that arrives at the gateway, and a switch, which furnishes the actual path in and out of the gateway for a given packet.
VoIP Adapter
VoIP Adapter Overview
What is a VoIP adapter?
A VoIP adapter is a device that converts analog voice signals into digital IP packets for transport over an IP network. A VoIP adapter also converts digital IP packets in analog voice streams.
Standard VoIP adapters connect to analog telephones via an FXS port. The VoIP adapter then connects to your Local Area Network (LAN) via an Ethernet cable and an RJ45 port. Some VoIP adapters also feature an FXO port so you can connect to the PSTN (Public Switched Telephone Network).
FXS and FXO Ports
FXS and FXO ports are important to know and not confuse. An FXS port is an interface that connects station devices such as your phones or PBX to a VoIP adapter. An FXO port is an interface that connects your POTS line to a VoIP adapter.
The number of telephones, PBX systems or POTS (Plain Old Telephone Service) lines you are looking to connect to a VoIP adapter determines how many of each port you will need.
How does a VoIP adapter work?
VoIP adapters are rather simple. A VoIP adapter works as a bridge between an IP network and an analog station device (desktop telephone) and or the PSTN. Depending on where the voice traffic originates from a VoIP adapter will convert voice traffic into the proper form for receipt by the destination network or device.
If the voice traffic is originating from an analog telephone or the PSTN a VoIP adapter will convert the analog voice signal into a digital signal. This digital signal is then compressed using a codec and broken into a series of packets that are transferred across the IP network using a signaling protocol.
If the voice traffic is originating from an IP network the VoIP adapter will decompress the digital packets into a digital signal that is then converted into an analog signal for receipt by the station device or sent across the PSTN.
A quick word about VoIP adapter protocols and codecs
If you’re only looking for a basic VoIP adapter for your home or business feel free to skim this next section. Protocols and codecs have a tendency to confuse people. Confused is the last thing you want to be. Now that the public service announcement is out of the way let’s learn more about protocols and codecs!
VoIP adapter protocols and codecs
Hopefully your head’s not spinning from the explanation of how a VoIP adapter works. Because it’s now time to talk about VoIP protocols and voice codecs. Even if you’re not technical you still need a basic understanding of VoIP protocols and codecs. In order for your adapter to work properly it must use a protocol and codec that is compatible with your VoIP phone system and or VoIP service. The protocol and codec you use can also drastically increase or decrease the quality of your calls.
VoIP protocols
A VoIP protocol determines how your voice packet is transported across a network. A VoIP adapter will typically support a single protocol. The most common VoIP protocols are:
• SIP (Session Initiation Protocol) – SIP is a standards-based protocol that is used and supported by the vast majority of VoIP phone systems and services.
• SCCP (Cisco Skinny Client Control Protocol) – SCCP is a proprietary protocol used by Cisco’s Call Manager and IP phones.
• MGCP – MGCP is an older VoIP protocol you might come across. It is no longer widely used and or supported.
• H.323 – Similar to MGCP, H.323 is an older VoIP protocol that you might come across, but is no longer widely used and or supported.
Voice codecs
A voice codec is responsible for the compression of your voice stream within a digital packet. It also determines sound quality and bandwidth required to send the packet. A VoIP adapter typically supports multiple voice codecs. The most common voice codecs are:
• GSM – 13 Kbps
• iLBC – 15 Kbps
• G.711 – 64 Kbps
• G.722 – 48/56/64 Kbps
• G.726 – 16/24/32/40 Kbps
• G.728 – 16 Kbps
• G.729 – 8 Kbps
Unless you’re the person responsible for the set-up, installation and maintenance of VoIP adapters for a VoIP service provider you don’t need to spend a ton of time worrying about protocols and codecs. Simply make sure your VoIP adapter supports the same protocols and codecs that your VoIP service and or VoIP phone system support.
Oh and if you are that person responsible for deploying thousands of VoIP adapters for a VoIP provider make sure you further your knowledge in the area of protocols and codecs.
The types of VoIP adapters
There are three different types of VoIP adapters. They include:
• Single FXS – A single FXS VoIP adapter allows you to connect one telephone. Single FXS VoIP adapters come with either one or two Ethernet ports.
• Dual FXS – A dual FXS VoIP adapter allows you to connect up to two telephones. Dual FXS VoIP adapters come with either one or two Ethernet ports.
• FXO / FXS – A FXO / FXS VoIP adapter allows you to connect a single telephone and a single POTS line. These combination adapters are typically used to provide fail-over or life-line capabilities.
Now you might be thinking, “What if I need to connect more than two telephones or POTS lines?” For that you’ll need a VoIP gateway. VoIP gateways perform the same essential functions as a VoIP adapter but are built to scale (up to 48 ports).
Features of a VoIP adapter
VoIP adapters are simple and so too are their features:
• Compliant with multiple protocols including SIP, H.323 and MGCP
• Support for G.711, G.723.1, G.726, and G.729A voice codecs
• T.38 compliant (for faxing)
• Echo cancellation, Jitter Buffer, VAD and CNG
• Web based administration/management
• Automatic provisioning via TFTP/HTTP
These are merely the standard features found in the majority of VoIP adapters. Each VoIP adapter will have its own subtle differences.
PBX
Private Branch Exchange – PBX
What is a PBX?
A PBX (Private Branch Exchange) is a switch station for telephone systems. It consists mainly of several branches of telephone systems and it switches connections to and from them, thereby linking phone lines.
Companies use a PBX for connecting all their internal phones to an external line. This way, they can lease only one line and have many people using it, with each one having a phone at the desk with different number. The number is not in the same format as a phone number though, as it depends on the internal numbering. Inside a PBX, you only need to dial three-digit or four-digit numbers to make a call to another phone in the network. We often refer to this number as an extension.
This picture shows what a PBX does.
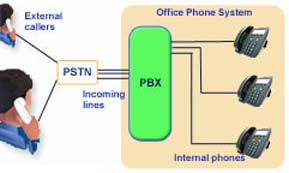
The Functions of a PBX
A PBX (Private Branch Exchange) is a switch station for telephone systems. It consists mainly of several branches of telephone systems and it switches connections to and from them, thereby linking phone lines.
Companies use a PBX for connecting all their internal phones to an external line. This way, they can lease only one line and have many people using it, with each one having a phone at the desk with different number. The number is not in the same format as a phone number though, as it depends on the internal numbering. Inside a PBX, you only need to dial three-digit or four-digit numbers to make a call to another phone in the network. We often refer to this number as an extension. A person calling from the outside might ask for an extension to be directed to the person she is targeting.
The main technical roles of a PBX are:
• To switch between telephone users thereby creating connections
• To make sure the connection remains in place properly by keeping its resources
• To properly end the connection when a user hangs up
• To record the quantities, statistics and metering related to the calls
Practically, the functions of a PBX are the following:
• Provide one single number that external callers can use to access all persons in a company.
• Distribute calls to employees in a answering team in an even way; using the Automatic Call Distribution (ACD) feature.
• Automate call answering, but offering a menu of options from which a user can select to be directed to a specific extension or department.
• Allow the use of customized business greetings while answering calls.
• Provide system call management features.
• Place external callers on hold while waiting for a requested person to answer, and playing music or customized commercial messages for the caller waiting.
• Record voice messages for any extension from an external caller.
• Transfer calls between internal extensions.
IP-PBX
PBXs are not only for VoIP but have been around for landline telephone systems as well. A PBX that is specifically made for VoIP is called an IP PBX, which stands for Internet Protocol Private Branch Exchange).
Up to now, PBXs have been a business luxury that only huge companies could afford. Now, with IP-PBXs, medium-sized and even some small companies can also benefit from the features and functionalities of a PBX while using VoIP. True they have to invest some money into hardware and software, but the return and benefits are considerable in the long term, both operationally and financially.
The main benefits that an IP-PBX brings around are scalability, manageability and enhanced features.
Adding, moving and removing users to an from a telephone system can be very costly, but with an IP-PBX it is as cost-effective as it is easy. Moreover, an IP phone (which represents terminals in a PBX phone network) may not necessary to attached to one specific user. Users can transparently log in the system through any phone in the network; without however losing their personal profiles and configurations.
IP-PBXs are more software based than their predecessors and so maintenance and upgrade costs are considerably reduced. The work is easier as well.
PBX Software
An IP-PBX needs a software to control its mechanism. The most popular PBX software is Asterisk which is a good open-source software.
Private branch exchange (PBX)
A PBX (private branch exchange) is a telephone system within an enterprise that switches calls between enterprise users on local lines while allowing all users to share a certain number of external phone lines. The main purpose of a PBX is to save the cost of requiring a line for each user to the telephone company’s central office.
The PBX is owned and operated by the enterprise rather than the telephone company (which may be a supplier or service provider, however). Private branch exchanges used analog technology originally. Today, PBXs use digital technology (digital signals are converted to analog for outside calls on the local loop using plain old telephone service (POTS ).
A PBX includes:
• Telephone trunk (multiple phone) lines that terminate at the PBX
• A computer with memory that manages the switching of the calls within the PBX and in and out of it
• The network of lines within the PBX
• A console or switchboard for a human operator (optional)
In some situations, alternatives to a PBX include centrex service (in which a pool of lines are rented at the phone company’s central office), key telephone systems, and, for very small enterprises, primary rate Integrated Services Digital Network (ISDN).
Private automatic branch exchange (PABX)
A PABX (private automatic branch exchange) is an automatic telephone switching system within a private enterprise. Originally, such systems – called private branch exchanges (PBX) – required the use of a live operator. Since almost all private branch exchanges today are automatic, the abbreviation “PBX” usually implies a “PABX.”
Some manufacturers of PABX (PBX) systems distinguish their products from others by creating new kinds of private branch exchanges. Rolm offers a Computerized Branch Exchange (CABX) and Usha Informatics offers an Electronic Private Automatic Branch Exchange (EPABX).
IP PBX (private branch exchange)
An IP PBX is a private branch exchange (telephone switching system within an enterprise) that switches calls between VoIP (voice over Internet Protocol or IP) users on local lines while allowing all users to share a certain number of external phone lines. The typical IP PBX can also switch calls between a VoIP user and a traditional telephone user, or between two traditional telephone users in the same way that a conventional PBX does. The abbreviation may appear in various texts as IP-PBX, IP/PBX, or IPPBX.
With a conventional PBX, separate networks are necessary for voice and data communications. One of the main advantages of an IP PBX is the fact that it employs converged data and voice networks. This means that Internet access, as well as VoIP communications and traditional telephone communications, are all possible using a single line to each user. This provides flexibility as an enterprise grows, and can also reduce long-term operation and maintenance costs. Like a traditional PBX, an IP PBX is owned by the enterprise.
What are the different types of private branch exchange (PBX) systems?
A PBX is the standard telephony system used in enterprises and is fairly common among small and medium-sized businesses. A PBX is known as a switched system, providing a centralized infrastructure for telephony. This allows for a consistent environment for all employees with access to the PBX, such as common features and an internal dialing plan with user-assigned extensions. From an IT perspective, the PBX allows for centralized control and management across the system.
Prior to the advent of Internet Protocol (IP), there really was just one type of PBX. The other options to a premise-based system would be a key telephone system or a central office exchange service (Centrex). The former is a scaled-down PBX, more suitable for smaller businesses with simpler needs. Centrex has long been a staple of campus environments that need PBX-like capabilities, but at a lower cost in the form of a hosted system that is leased rather than owned.
With IP now becoming the standard for telephony, the PBX has evolved into the IP PBX. Legacy PBX systems still account for most of today’s installed base, but the vast majority of new purchases and upgrades are IP PBX. The systems are similar at their cores, but IP-based systems are less capital-intensive and offer more flexibility in terms of adding new features and integrating VoIP with other communication modes.
RFID
Radio Frequency Identification – RFID
What is RFID?
Radio frequency identification, or RFID, is a generic term for technologies that use radio waves to automatically identify objects. There are several methods of identification, but the most common is to store a serial number that identifies the object and perhaps other information, on a microchip that is attached to an antenna (the chip and the antenna together are called an RFID transponder or an RFID tag). The antenna enables the chip to transmit the identification information to a reader. The reader converts the radio waves emitted by the RFID tag into digital information that can then be passed on to computers that can make use of it.
History of RFID
Radio Frequency Identification (RFID) is actually not as new as most people might think. RFID was developed out of the radar experiments and development during the Second World War. The actual date of invention is 1948 but this was followed by decades of development and experimentation before commercial applications were implemented. In 1987 Norway implemented the first successful toll collection system. Toll systems were the breakthrough product for RFID.
What are the Major Components of an RFID System?
Deploying a radio frequency identification system that delivers true business value involves much more than purchasing the right tags and installing the right readers. To get business value from the all of the information collected, companies also need middleware to filter the collected raw tag data.
Tags and Readers
Tags and readers are the main components of an RFID system. There are two basic types of tags, active and passive. Active RFID tags have a transmitter and their own power source (typically a battery). The power source is used to run the microchip’s circuitry and to broadcast a signal to a reader (the way a cell phone transmits signals to a base station). Passive tags have no battery. Instead, they draw power from the reader, which sends out electromagnetic waves that induce a current in the tag’s antenna. Semi-passive tags use a battery to run the chip’s circuitry, but communicate by reflecting power from the reader.
Readers can house internal or external antennas. Readers with external antennas can have one or more ports for connecting additional antennas. Readers can also have input/output ports for connecting to external devices. An input port might be connected to an electric eye that activates the reader when something passes through its field of view. An output port might connect to a programmable logic controller, conveyor sorter or other device controlled by the reader. Readers also have ports for connecting to a computer or network.
Middleware
Middleware is a generic term used to describe software that resides between the RFID reader and enterprise applications. The middleware takes raw data from the reader (which might read the same tag 100 times per second), filters it and passes on the useful event data to back-end systems. Middleware can play a key role in getting the right information to the right application at the right time.
What are Active RFID Systems?
Active tags may be broadly operated in one of two operational modes: as transponders and/or as beacons. Active transponders are awakened when they receive a signal from a reader. Popular applications are in toll payment collection, checkpoint control and other choke-point systems. For example when a car with an active transponder approaches a tollbooth, a reader at the booth sends out a signal that activates the transponder on the car windshield. The transponder then transmits its unique ID to the reader. In this manner, transponders conserve battery life by enabling the tag to send a signal only when it is within range of a reader.
Active beacons are utilized in real-time locating systems (RTLS) that cannot accommodate choke points. A beacon emits a signal with its unique identifier at pre-set intervals, for example, once every second, every minute, every hour, or several times per day, depending on the urgency of the location tracking application.
Active tags can be read reliably because they transmit (rather than reflect) a signal to the reader. Read ranges of 100 meters (greater than 300-feet) is common, but range often depends on the antenna type, environmental factors, and regulatory constraints. Active tags can cost from $10 to a few hundred dollars, depending on their capability, amount of memory, battery life, and integrated sensor functionality.
RFID Will Enable Any Organization to Better Understand Their Operations
The goal of a radio-frequency identification (RFID) system is to generate data that can be acted on to boost efficiency, cut costs or provide other business benefits. Active RFID, which has a power source in a tag, is becoming a rapidly growing ‘sleeper’ technology. Active RFID will create a competitive advantage in consumer goods, combat the new terrorism, other crime and threatened epidemics of disease and will serve consumers and governments demanding better service, more information, food traceability and condition monitoring. The safety of construction and the risk of natural disasters will be monitored by Ubiquitous Sensor Networks (USNs) as a form of active RFID, and they will assist and monitor the increasing number of elderly and disabled.
Pearl PDA800 series products support 13.56M Hz RFID card. PES3202 supports Wi-Fi location function.
Radio
Radio
What is a Radio?
A radio is transmission of signals where no wires are required, and which uses the modulation of electromagnetic waves with frequencies below that of visible light. Although it was Nikola Tesla who first demonstrated the feasibility of wireless communications in 1893, Guglielmo Marconi, an Italian inventor, was the first to develop workable radio communication. In Italy, he sent and received his first radio signal in the year 1895. Lots of experiments were carried out with the radio, but it was in the early 1930s that amateur radio operators invented single sideband and frequency modulation.
In 1954, Regency introduced a pocket transistor radio, the TR-1, powered by a ‘standard 22.5 V battery’. However in 1960, Sony introduced its first transistorized radio, which was small enough to fit in a vest pocket, and was powered by a small battery. Over the next 20 years, except for very high-power uses, transistors replaced tubes almost completely. In the early 1990s, amateur radio experimenters were using personal computers with audio cards to process radio signals, and in the year 1994, the US Army launched an aggressive, successful project to construct a software radio that was to become a different radio on the fly by changing software.
Radio Broadcasting
Radio broadcasting is the distribution of audio signals that transmit programs to an audience. There are wide varieties of broadcasting systems, all of which have different capabilities. It can vary from limited area coverage to national coverage, and can be used to transmit signals globally too, using retransmitted towers, satellite systems, and cable distribution. Satellite radio revolutionaries the entire scenario, it could cover even wider areas, such as entire continents, and Internet channels can distribute text or streamed music worldwide. In the late 1990s, digital transmissions began to be applied to broadcasting.
A broadcast may be distributed through several physical means. If coming directly from the studio at a single station, then it is simply sent to the transmitter from the antenna on the tower. Programming which comes through a satellite, is played either live or recorded for transmission later. Different stations may simulcast the same programming at the same time. Usually, analog or digital tapes or CDs/DVDs are included in another broadcast. The final stage of broadcasting is to get the signal to the audiences. It is done via a station to a receiver or through cable. Internet also brings radio to the recipient.
Internet Radio
Internet radio is an audio broadcasting service transmitted via the Internet. Broadcasting on the Internet is usually referred to as web casting since it is not transmitted broadly through wireless means, but is delivered over the World Wide Web. Internet radio is usually accessible from anywhere in the world. These live radio stations on the Web make it a popular service since everything that is on the radio station is simulcast over the Internet with a net cast stream.
Commercial interests of corporate giants have proven to be a boon to listeners all over the world. I wish this continues and we all benefit from this, at least once for the sake of history, common man will be benefited by war of these big commercial giants. I fancy the day when telepathy will become so strong that we will not require any physical means to communicate, no words―just complete silence and peace and that every one will become a transmitter and a receiver. The rate at which we have grown in past few centuries―who knows someday all our fancies may come true.
Radio Frequencies
Radio frequency waves are high frequency waves. This technology finds uses in various fields. Radio frequency or RF is a frequency or rate of oscillation in the range of 3 Hz to 300 Ghz. This range relates to the frequency of alternating current signals to create and detect radio waves. As this range is beyond the vibration rate that many mechanical systems respond to, RF refers to oscillations in electrical circuits. When the current is passed through an antenna, an electromagnetic field is generated that is suitable for wireless broadcasting and/or communication. These frequencies cover the electromagnetic radiation spectrum ranging from 9 kHz, the lowest allocated wireless communications frequency, to thousands of gigahertz. When an RF current is passed through an antenna, an electromagnetic field is created that propagates through space.
Properties of Radio Frequency Electrical Signals
They can be ionized easily to create a conductive path across air
The electromagnetic force that drives the RF current to the surface of conductors known as skin effect
They have the ability to appear to flow through paths containing insulating material similar to the dielectric insulator of the capacitor
Radio spectrum
Extremely low frequency – 3 to 30 Hz
Super low frequency – 30 to 300 Hz
Ultra low frequency – 300 Hz to 3 Khz
Very low frequency – 3 Khz to 30 Khz
Low frequency – 30 Khz to 300 Khz
Medium frequency – 300 Khz to 3 Mhz
High frequency – 3 Mhz to 30 Mhz
Very high frequency – 30 Mhz to 300 Mhz
Ultra high frequency – 300 Mhz to 3 Ghz
Super high frequency – 3 Ghz to 30 Ghz
Extremely high frequency – 30 Ghz to 300 Ghz
Radio Frequency Encoding
These techniques physically encapsulate an RF encodable microchip with the synthesis resin. The RF transponder can be scanned post-synthesis to identify the concerned product. RF encoding avoids the need to cosynthesize surrogate analytes, and permits the large-scale synthesis of compounds; each microcapsule can hold tens milligrams of synthesis beads.
Radio Frequency Identification
This is an automatic identification method. RFID tags or transponders are used for storing and remotely retrieving data. An RFID tag is an object that can be applied in a product, animal or person to help in its identification using radiowaves. Some tags can be read beyond the line of sight of the reader. These tags consist of two parts. One is an integrated circuit for storing and processing information, modulating and demodulating signals, and for other specialized functions. The second is an antenna used for receiving and transmitting the signal. Chipless RFID discretely identifies tags in the absence of an integrated circuit. So, tags are printed directly on assets, and this helps lower its production cost.
RFID Tag Types
The various types of tags are as follows:
Passive : There is no internal power supply. The practical read distances range from 10 cm to a few meters, depending on the selected radio frequency and antenna design/size
Active : There is an internal power source. The range is of hundreds of meters, and the battery life is about 10 years
Semi-passive : They have their own power source. The battery powers the microchip, and cannot broadcast any signal
Use of RFID technology
RFID chips for animals are very small devices injected through a syringe under the skin
Real-time inventory tracking allows companies to control supply
RFID systems are used in some hospitals to track a patient’s location, doctors, and nurses
Traffic monitoring system uses roadside readers to collect signals from transponders
RTLS
Real-time Locating System – RTLS
Real-time locating systems (RTLS) are used to automatically identify and track the location of objects or people in real time, usually within a building or other contained area. Wireless RTLS tags are attached to objects or worn by people, and in most RTLS, fixed reference points receive wireless signals from tags to determine their location.
Examples of real-time locating systems include tracking automobiles through an assembly line, locating pallets of merchandise in a warehouse, or finding medical equipment in a hospital.
The physical layer of RTLS technology is usually some form of radio frequency (RF) communication, but some systems use optical (usually infrared) or acoustic (usually ultrasound) technology instead of or in addition to RF. Tags and fixed reference points can be transmitters, receivers, or both, resulting in numerous possible technology combinations.
RTLS are a form of local positioning system, and do not usually refer to GPS, mobile phone tracking. Location information usually does not include speed, direction, or spatial orientation.
Applications
RTLS can be used numerous logistical or operational areas such as:
1. locate and manage assets within a facility, such as finding a misplaced tool cart in a warehouse or medical equipment
2. notification of new locations, such as an alert if a tool cart improperly has left the facility
3. to combine identity of multiple items placed in a single location, such as on a pallet
4. to locate customers, for example in a restaurant, for delivery of food or service
5. to maintain proper staffing levels of operational areas, such as ensuring guards are in the proper locations in a correctional facility
6. to quickly and automatically account for all staff after or during an emergency evacuation
7. To automatically track and time stamp the progress of people or assets through a process, such as following a patient’s emergency room wait time, time spent in the operating room, and total time until discharge. Such a system can be used for process improvement
8. clinical-grade locating to support acute care capacity management
NFC
Near Field Communication – NFC
Near field communication, abbreviated NFC, is a form of contactless communication between devices like smartphones or tablets. Contactless communication allows a user to wave the smartphone over a NFC compatible device to send information without needing to touch the devices together or go through multiple steps setting up a connection. Fast and convenient, NFC technology is popular in parts of Europe and Asia, and is quickly spreading throughout the United States.
- What is near field communication (NFC)?
? Near field communication uses electromagnetic radio fields to allow two compatible devices to exchange data and share information when passed close to each other. Typically the devices must be within four to five centimeters of each other to work. This is in contrast to far field communication which operates across great distances.
- How does NFC work?
? Your smartphone or other NFC compatible device sends out radio frequency signals that interact with an NFC tag found in compatible card readers and smart posters. The signal creates a current that flows through the NFC tag and allows the device and the tag to communicate with one another. Typically one device, the tag, is passive and only sends out information while the other device, the smartphone in this case, is active and can both send and receive information.
- How does NFC benefit individuals?
? NFC provides numerous ways to make payments, retrieve information, and even exchange videos or information with friends on the go. Swiping your smartphone at a supermarket checkout instantly pays for your groceries without digging into your wallet for a credit card. Passing your phone over a friend’s phone allows you to share a website link while waving the phone in front of a poster or display with a NFC tag in it shows information about what you’re viewing. This is an excellent way to learn more about exhibits in a museum or upcoming events in your community.
- How does NFC benefit businesses and non-profit organizations?
? NFC allows your business to provide fast, secure ways for customers to pay at the register without digging through their wallets for various credit cards. It also lets customers store coupons and redeem customer loyalty points without carrying around extra papers and cards. It also offers ways to send information to customers using smart posters and displays with a NFC tag inside. A visitor would swipe their phone to learn more about historic monuments or famous pieces of artwork.
- Is NFC only for smartphones?
? Not at all! Many devices, be it a smartphone or a tablet, are capable of reading NFC tags.
- Is my smartphone NFC compatible?
?Some smartphones have NFC integrated into the smartphone itself while others can use NFC when a SIM card or microSD card compatible with NFC is installed. Checking your phone manufacturer’s website and pulling up your specific model should present a list of features and will include NFC if it is available. Well-known NFC compatible phones include Google’s Nexus S, Samsung’s Galaxy S II, and the BlackBerry Bold (versions 9900 and 9930).
- Can I still use NFC technology if my smartphone isn’t compatible?
? Yes. Near field communication technology is expanding and will be available on both SIM cards and microSD cards. Purchasing one of these two cards and inserting it into your smartphone lets you use NFC technology as long as you don’t remove the card.

